Published
- 8 min read
eBPF: The Revolutionary Linux Kernel Technology

eBPF: The Revolutionary Linux Kernel Technology
Extended Berkeley Packet Filter (eBPF) represents one of the most significant innovations in Linux kernel development in recent years. This revolutionary technology allows developers to run sandboxed programs directly in the kernel space without modifying kernel source code or loading kernel modules[1]. eBPF has transformed how we approach networking, security, observability, and performance monitoring in modern Linux systems, enabling unprecedented levels of programmability and efficiency[2].
Originally designed as an extension to the Berkeley Packet Filter for network packet filtering, eBPF has evolved into a universal in-kernel virtual machine that provides hooks throughout the Linux kernel[3][4]. Major technology companies including Google, Netflix, Meta, and Cloudflare have adopted eBPF at scale for various production workloads, from processing every packet entering Meta’s data centers to providing network insights at Netflix[5]. The technology’s safety guarantees, performance benefits, and versatility have made it the preferred approach for kernel-level programming over traditional kernel modules.
Understanding eBPF Architecture
The eBPF Virtual MachineeBPF operates as a register-based virtual machine within the Linux kernel, featuring eleven 64-bit registers, a program counter, and a 512-byte stack space[2]. The virtual machine executes eBPF programs written in a restricted subset of C, which are compiled into eBPF bytecode and then either interpreted or Just-In-Time (JIT) compiled to native machine instructions for optimal performance[6].The eBPF instruction set closely resembles contemporary processor architectures, enabling efficient one-to-one mapping between eBPF instructions and native machine code[6]. This design choice significantly reduces the overhead associated with program execution and allows eBPF programs to achieve near-native performance while maintaining safety guarantees through the kernel’s verification process[2].
Safety Through Verification
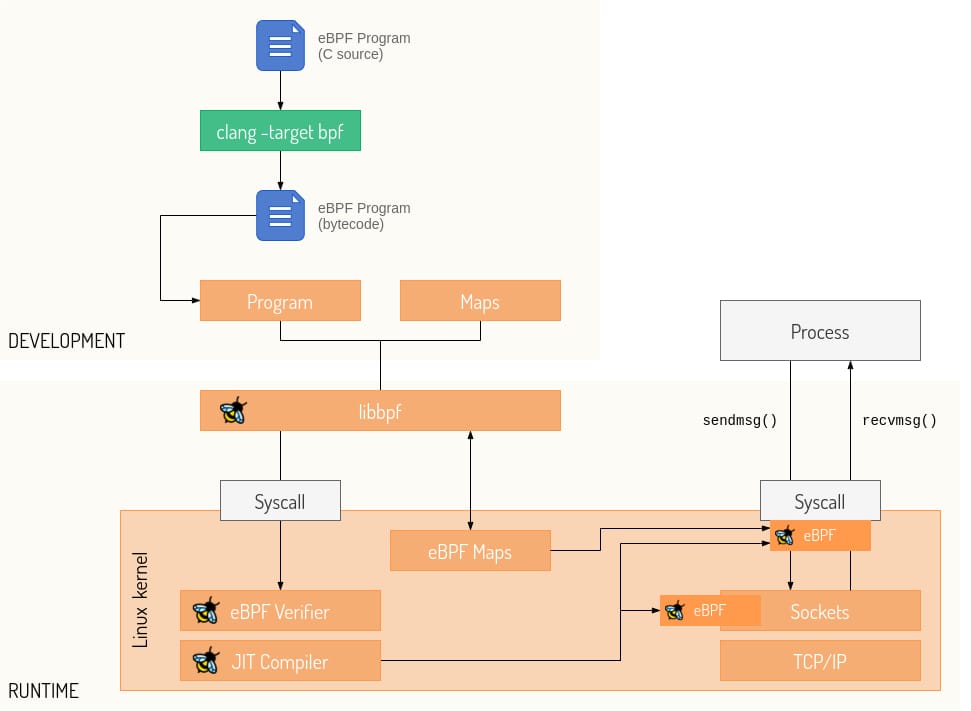 The eBPF verifier serves as the critical gatekeeper ensuring program safety before execution[7]. This sophisticated static analysis engine performs multiple validation steps, including Control Flow Graph (CFG) validation to prevent infinite loops, bounds checking to prevent out-of-bounds memory access, and type safety verification to ensure proper register usage[8]. The verifier’s rigorous checking process guarantees that eBPF programs cannot crash the kernel, leak sensitive information, or violate system security policies[9].
The eBPF verifier serves as the critical gatekeeper ensuring program safety before execution[7]. This sophisticated static analysis engine performs multiple validation steps, including Control Flow Graph (CFG) validation to prevent infinite loops, bounds checking to prevent out-of-bounds memory access, and type safety verification to ensure proper register usage[8]. The verifier’s rigorous checking process guarantees that eBPF programs cannot crash the kernel, leak sensitive information, or violate system security policies[9].
eBPF Maps:
Data Structures for CommunicationeBPF maps provide efficient key-value storage mechanisms that enable data sharing between eBPF programs and user-space applications[10]. These generic data structures support various types including hash tables, arrays, ring buffers, and specialized structures like LRU caches and longest prefix match tries[11]. Maps serve multiple purposes: storing program state, facilitating communication between kernel and user space, and enabling complex data processing workflows[10].
Core Benefits and Applicationse
BPF’s versatility stems from its ability to attach to numerous kernel hooks and events, enabling diverse use cases across different domains[12]. The technology’s benefits span performance optimization, security enhancement, deep observability, and programmable networking capabilities.### Performance and EfficiencyeBPF programs execute directly in kernel space, eliminating the overhead of context switching between user and kernel modes[13]. This architectural advantage enables significant performance improvements, with some applications achieving up to 95% better packet processing rates compared to traditional approaches[13]. The technology’s efficiency makes it particularly valuable for high-performance networking applications and real-time monitoring systems[14].
Security and Compliancee
BPF enables runtime security enforcement through programmable policy engines that can monitor, filter, and block potentially malicious activities[15]. Security applications include intrusion detection systems, runtime application self-protection (RASP), and compliance monitoring[16]. The technology’s ability to observe system calls, network traffic, and file operations provides comprehensive visibility for security analysis[17].
Observability and Debugging
The technology excels in providing deep system insights through its comprehensive tracing capabilities[18]. eBPF programs can attach to various instrumentation points including kprobes, tracepoints, and user-space probes, enabling detailed analysis of system behavior[19]. This capability has revolutionized debugging and performance analysis, allowing developers to gain unprecedented visibility into system operations[13].
eBPF Hook Types and Applicationse
BPF’s power comes from its ability to attach to numerous hook points throughout the Linux kernel, each serving specific use cases and providing different levels of access to system resources[12].### Network HooksXDP (eXpress Data Path) represents one of eBPF’s most powerful networking capabilities, enabling high-performance packet processing at the earliest point in the network stack[20]. XDP programs can process, modify, or drop packets before they enter the kernel’s network stack, achieving 26 million packets per second per core on commodity hardware[20]. Traffic Control (TC) hooks provide another networking attachment point, allowing eBPF programs to shape, redirect, or filter traffic at the kernel’s traffic control layer[14].
Tracing Hooks
Tracing hooks enable comprehensive system monitoring through dynamic instrumentation[19]. Kprobes allow attachment to almost any kernel function, while tracepoints provide stable interfaces to kernel events[12]. User-space probes (uprobes) extend tracing capabilities to user-space applications, enabling end-to-end observability across the entire system stack[12].
Security Hooks
Linux Security Module (LSM) hooks integrate eBPF with the kernel’s security framework, enabling programmable security policies[12]. These hooks can enforce access controls, monitor sensitive operations, and implement custom security policies at the kernel level[17].
Development Frameworks and Tools
BCC vs. libbpf
The eBPF development ecosystem offers multiple frameworks catering to different development needs and preferences[21]. BCC (BPF Compiler Collection) provides a Python-based development environment with runtime compilation, making it excellent for rapid prototyping and scripting[22]. However, BCC requires Clang/LLVM libraries on target systems, increasing deployment complexity[21].
libbpf represents the modern approach to eBPF development, supporting CO-RE (Compile Once, Run Everywhere) capabilities[21]. This framework generates portable binaries that can run across different kernel versions without requiring compilation dependencies on target systems[21]. libbpf’s approach reduces application size and resource consumption while improving deployment flexibility[21].
Development Workflow
Modern eBPF development follows a structured workflow involving program compilation, verification, loading, and attachment[23]. Developers write eBPF programs in restricted C, compile them to eBPF bytecode using LLVM/Clang, and load them into the kernel using the bpf() system call[6]. The kernel’s verifier validates program safety before allowing execution, ensuring system integrity[6].
Real-World Applications and Case Studies
Networking and Load Balancing
Major technology companies leverage eBPF for high-performance networking applications[5]. Meta processes every packet entering their data centers using eBPF programs, while Cloudflare uses eBPF for DDoS mitigation and traffic shaping[5]. These applications demonstrate eBPF’s capability to handle massive traffic loads while maintaining kernel integration[5].
Security and Monitoring
Organizations like Capital One and Apple use eBPF for security monitoring and threat detection[5]. The technology’s ability to observe system calls, network connections, and file operations provides comprehensive security visibility[24]. eBPF-based security tools can detect anomalous behavior, enforce policies, and respond to threats in real-time[15].
Observability and Performance Analysis
Netflix employs eBPF for network performance analysis and infrastructure optimization[5]. The company has developed tools like bpftop for monitoring eBPF program performance, demonstrating the technology’s value for operational visibility[25]. These applications showcase eBPF’s capability to provide detailed insights into system behavior with minimal overhead[25].
Getting Started with eBPF
Hello World: Your First eBPF Program
Getting started with eBPF involves understanding its basic structure and development process[23]. A simple “Hello World” program demonstrates the fundamental concepts:
#include
#include
char LICENSE[] SEC("license") = "GPL";
SEC("tp/syscalls/sys_enter_write```int handle_write(void *ctx) {
bpf_printk("Hello, ```F World!\n");
return 0;
}This program attaches to the write system call tracepoint and prints a message when triggered[23]. The SEC macro specifies the program section, enabling proper loading and attachment[19].
Development Environment Setup
Setting up an eBPF development environment requires several components[23]:
- Modern Linux kernel (4.8+ minimum, 5.15+ recommended)
- LLVM/Clang compiler toolchain
- libbpf development libraries
- BPF development tools (bpftool, bcc-tools)
These tools provide the foundation for eBPF development, from compilation to debugging and deployment[23].
Best Practices and Considerations
Successful eBPF deployment requires attention to several key areas[18]:
- Program complexity management to avoid verifier limitations
- Map design optimization for efficient data structures
- Resource usage monitoring to prevent performance impact
- Security considerations for privilege management
- Version compatibility across different kernel versions
Future Directions and Conclusion
eBPF continues to evolve rapidly, with ongoing developments in hardware offloading, expanded hook points, and enhanced development tools[6]. The technology’s success has led to ports to other operating systems, including Microsoft’s eBPF for Windows[2]. As cloud-native architectures become increasingly complex, eBPF’s ability to provide programmable, efficient, and safe kernel-level functionality becomes ever more valuable[1].
The revolutionary nature of eBPF lies not just in its technical capabilities, but in its paradigm shift toward dynamic kernel programmability[1]. By enabling safe, efficient kernel programming without traditional barriers, eBPF has democratized kernel development and opened new possibilities for system optimization, security enhancement, and operational visibility[2]. As Linus Torvalds noted, “BPF has actually been really useful, and the real power of it is how it allows people to do specialized code that isn’t enabled until asked for”[2].
For developers and system administrators looking to leverage modern Linux capabilities, eBPF represents an essential technology that bridges the gap between performance and safety, enabling innovative solutions to complex system challenges[1]. The future of Linux kernel programming increasingly points toward eBPF as the preferred approach for extending system capabilities while maintaining the stability and security that production environments demand[2].
- [1] https://ebpf.io/what-is-ebpf/
- [2] https://en.wikipedia.org/wiki/EBPF
- [3] https://www.sentinelone.com/cybersecurity-101/cybersecurity/what-is-extended-berkeley-packet-filter-ebpf/
- [4] https://prototype-kernel.readthedocs.io/en/latest/bpf/
- [5] https://ebpf.io/case-studies/
- [6] https://arxiv.org/html/2410.00026v2
- [7] https://www.linuxfoundation.org/press/threat-model-and-independent-verifier-audit-examine-the-security-of-ebpf
- [8] https://docs.kernel.org/bpf/verifier.html
- [9] https://docs.ebpf.io/linux/concepts/verifier/
- [10] https://docs.ebpf.io/linux/concepts/maps/
- [11] https://prototype-kernel.readthedocs.io/en/latest/bpf/ebpf_maps.html
- [12] https://eunomia.dev/others/miscellaneous/ebpf-usecases/
- [13] https://tuxcare.com/blog/ebpf-for-advanced-linux-performance-monitoring-and-security/
- [14] https://www.datadoghq.com/blog/xdp-intro/
- [15] https://www.upwind.io/glossary/what-is-ebpf-security
- [16] https://www.oligo.security/academy/ebpf-security-top-5-use-cases-challenges-and-best-practices
- [17] https://www.linuxfoundation.org/hubfs/eBPF/ControlPlane%20%E2%80%94%20eBPF%20Security%20Threat%20Model.pdf
- [18] https://www.groundcover.com/ebpf/ebpf-tracing
- [19] https://falco.org/blog/tracing-syscalls-using-ebpf-part-1/
- [20] https://en.wikipedia.org/wiki/Express_Data_Path
- [21] https://devops.com/libbpf-vs-bcc-for-bpf-development/
- [22] https://github.com/iovisor/bcc
- [23] https://eunomia.dev/en/tutorials/1-helloworld/
- [24] https://www.armosec.io/blog/ebpf-use-cases/
- [25] https://netflixtechblog.com/announcing-bpftop-streamlining-ebpf-performance-optimization-6a727c1ae2e5
- [26] https://www.kentik.com/kentipedia/what-is-ebpf-extended-berkeley-packet-filter/
- [27] https://github.com/eunomia-bpf/bpf-developer-tutorial
- [28] https://ebpf.io/applications/
- [29] https://cilium.isovalent.com/hubfs/Learning-eBPF%20-%20Full%20book.pdf
- [30] https://www.aquasec.com/cloud-native-academy/devsecops/ebpf-linux/
- [31] https://en.wikipedia.org/wiki/Berkeley_Packet_Filter
- [32] https://www.groundcover.com/ebpf
- [33] https://github.com/lizrice/ebpf-networking
- [34] https://www.reddit.com/r/kubernetes/comments/vsyf0x/what_exactly_is_an_extended_berkeley_packet/
- [35] https://ebpf.io/get-started/
- [36] https://github.com/zoidyzoidzoid/awesome-ebpf
- [37] https://www.datadoghq.com/knowledge-center/ebpf/
- [38] https://developers.redhat.com/articles/2023/10/19/ebpf-application-development-beyond-basics
- [39] https://eunomia.dev/en/tutorials/
- [40] https://events.linuxfoundation.org/wp-content/uploads/2023/08/Vandana-Salve-Mentorship-8-2-23-KernelTracing_eBPF.pdf
- [41] https://bpfman.io/v0.5.0/getting-started/example-bpf/
- [42] https://www.collabora.com/news-and-blog/blog/2019/04/05/an-ebpf-overview-part-1-introduction/
- [43] https://blog.px.dev/ebpf-probes-and-you/
- [44] https://www.tigera.io/learn/guides/ebpf/
- [45] https://ebpf.io
- [46] https://grafana.com/grafana/dashboards/18612-kernel-ebpf-hook/
- [47] https://www.tigera.io/learn/guides/ebpf/ebpf-xdp/
- [48] https://sematext.com/blog/linux-kernel-observability-ebpf/
- [49] https://lwn.net/Articles/740157/
- [50] https://www.infoq.com/articles/gentle-linux-ebpf-introduction/
- [51] https://www.meegle.com/en_us/topics/ebpf/ebpf-software-development-frameworks-design
- [52] https://newrelic.com/blog/best-practices/what-is-ebpf
- [53] https://sookocheff.com/post/ebpf/surveying-the-ebpf-developer-ecosystem/
- [54] https://www.cequence.ai/blog/api-security/ebpf-for-api-security/
- [55] https://www.redhat.com/en/blog/monitoring-ebpf-based-metrics
- [56] https://www.iovisor.org/technology/xdp
- [57] https://tma.ifip.org/2024/wp-content/uploads/sites/13/2024/06/eBPF_SebastianoMiano_1tutorial_2.pdf
- [58] https://toonk.io/building-an-xdp-express-data-path-based-bgp-peering-router/index.html
- [59] https://stackoverflow.com/questions/77444624/how-to-design-ebpf-map-for-large-data-structures-without-exceeding-jump-complexi
- [60] https://www.linuxfoundation.org/hubfs/eBPF/eBPF%20Verifier%20Security%20Audit.pdf
- [61] https://github.com/xdp-project/xdp-tutorial
- [62] https://docs.kernel.org/bpf/maps.html
- [63] https://www.usenix.org/system/files/osdi24-sun-hao.pdf
- [64] https://courses.grainger.illinois.edu/ece598hpn/fa2023/slides/lect18-xdp.pdf
- [65] https://docs.ebpf.io/linux/map-type/
- [66] https://github.com/google/security-research/security/advisories/GHSA-hfqc-63c7-rj9f
- [67] https://builders.intel.com/university/course/express-data-path-xdp-and-address-family-express-data-path-af_xdp